Alex
Legacy SSH Enabler (LSSHE)
By Alex Free.
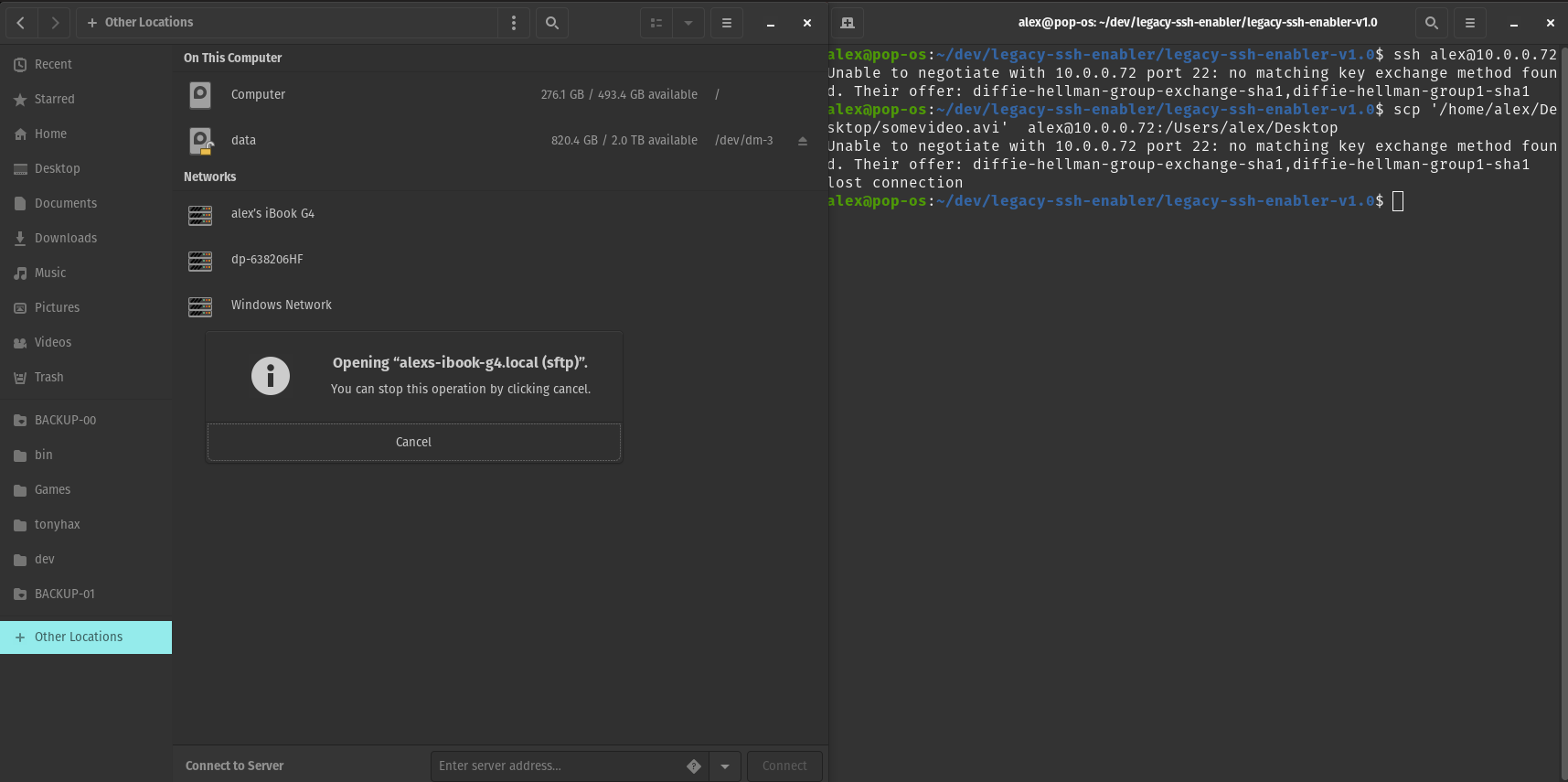
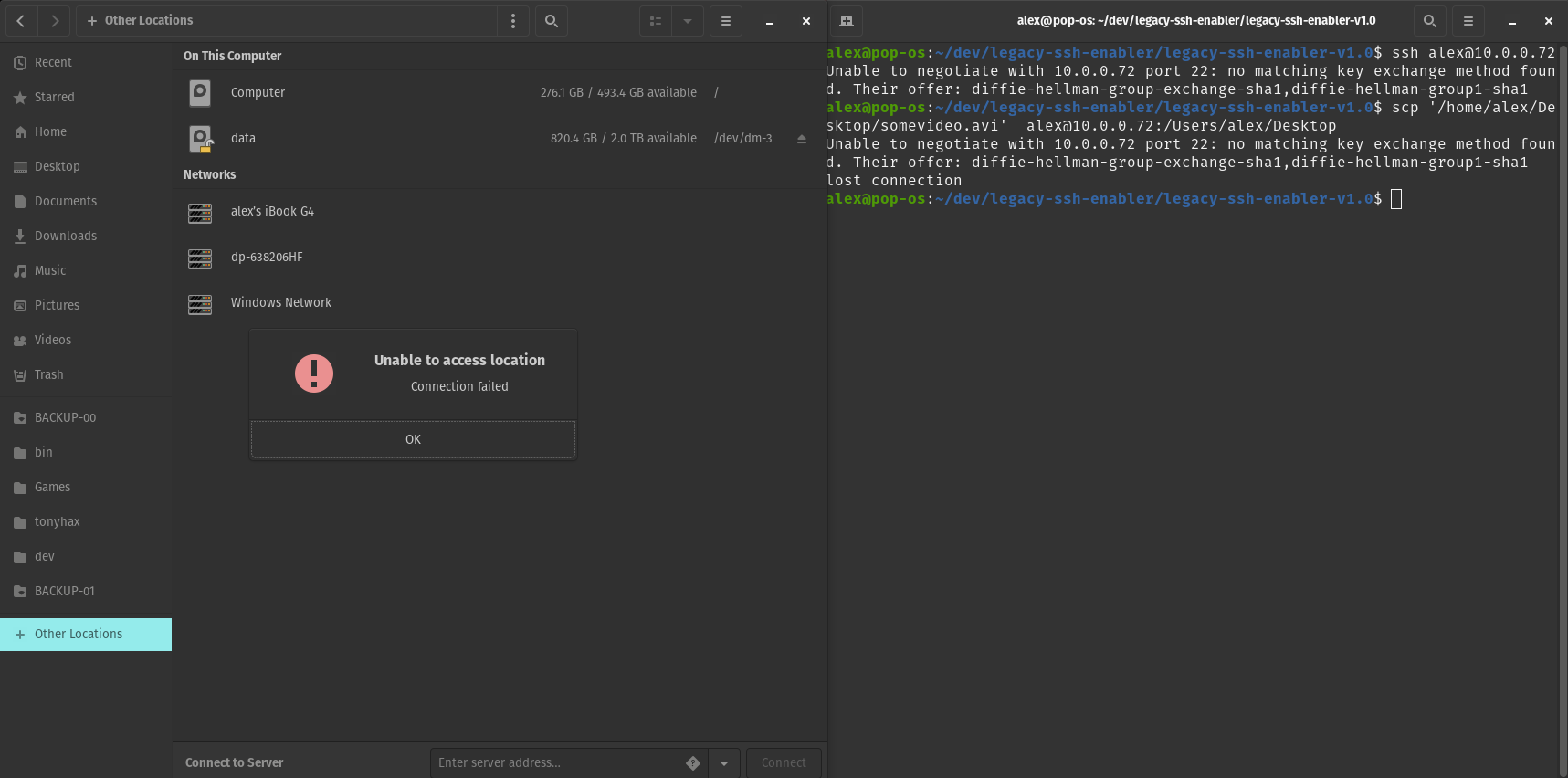
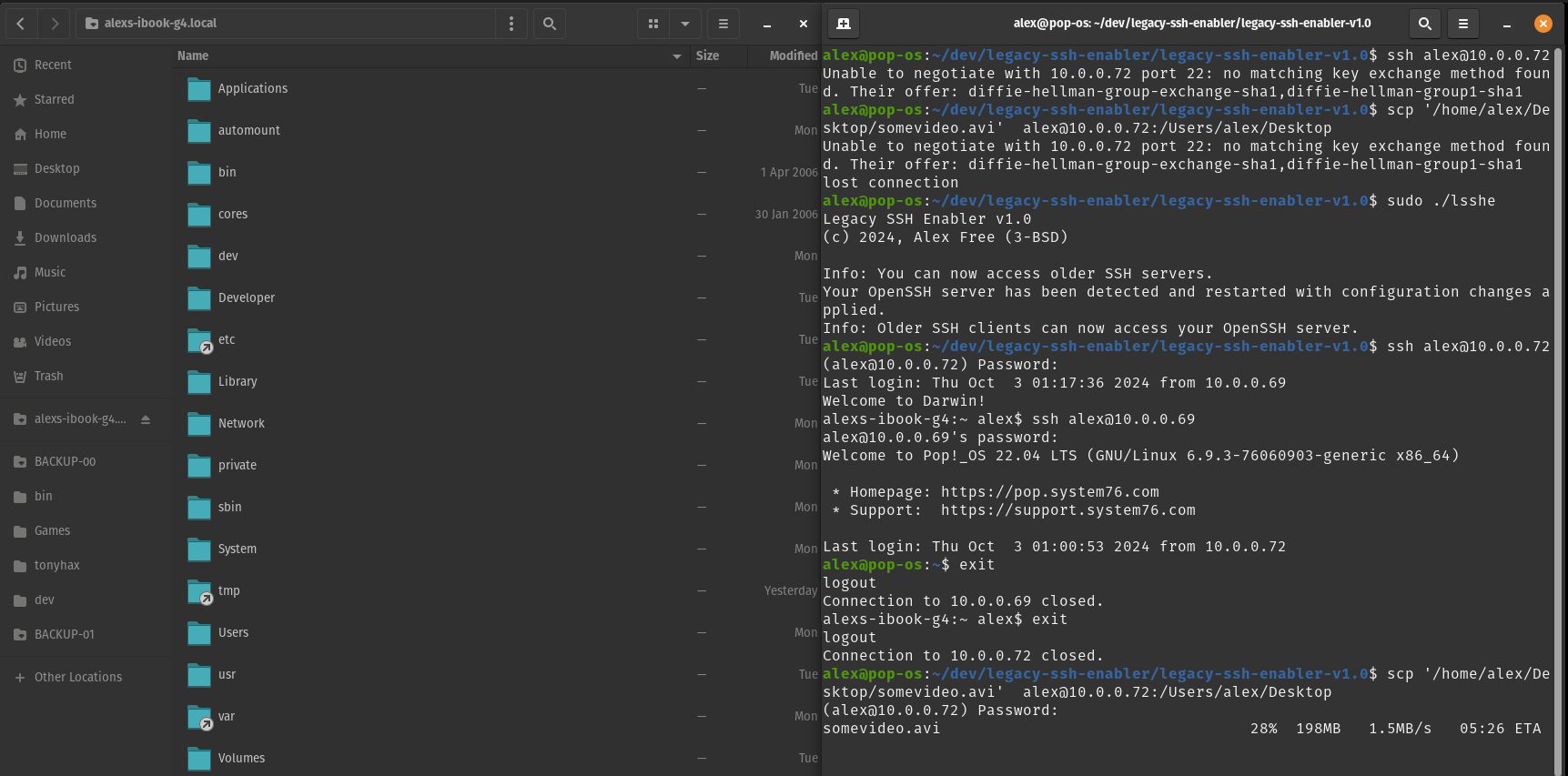
Legacy SSH Enabler fixes errors encountered when using a newer OpenSSH client to connect to an older SSH server (i.e. Unable to negotiate with 10.0.0.72 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group1-sha1). It also fixes errors encounter when using an older SSH client to connect to a newer OpenSSH server (i.e. no kex alg). Mac OS and Linux are supported!
| Homepage | Github |
Table Of Contents
- Downloads
- Usage
- Before Legacy SSH Enabler
- After Legacy SSH Enabler
- Why Is This Needed?
- How Does This Work?
- License
- Building
Downloads
Version 1.0.1 (3/6/2025)
Changes:
-
Implemented proper support for RedHat Linux distros (Fedora, CentOS, RHEL). RSAMinSize is now set to 768, and update-crypto-policies is now set to LEGACY.
-
It works on Mac OS! It already did, but I didn’t expect it to or document it (just needs SIP disabled).
-
legacy-ssh-enabler-v1.0.1.zip Portable zip release for Linux and Mac OS
-
legacy-ssh-enabler-v1.0.1.deb DEB package file for Linux
-
legacy-ssh-enabler-1.0-1.noarch.rpm RPM package file for Linux
Usage
If you have Mac OS, you need to disable SIP (System Integrity Protection) before continuing.
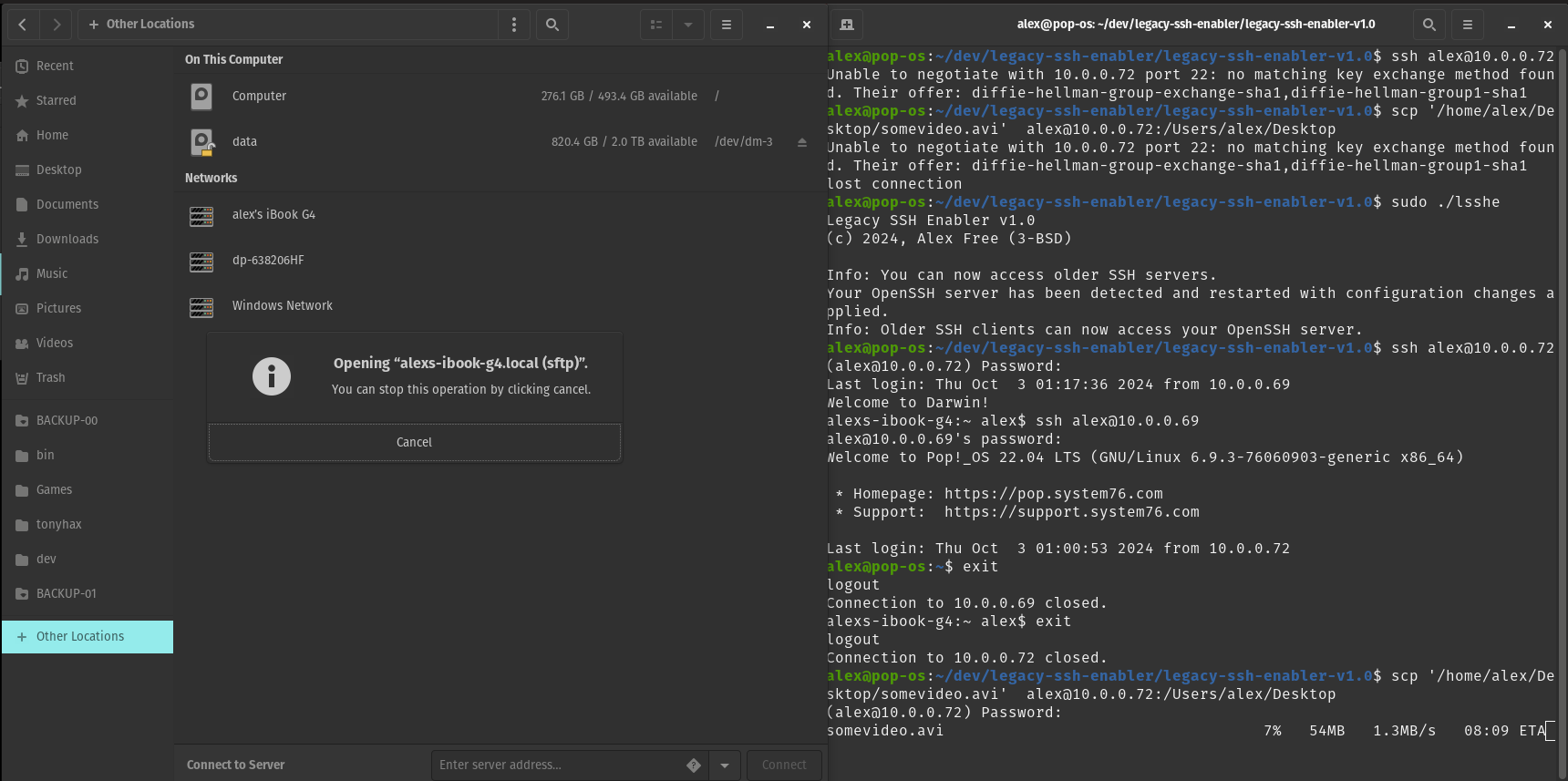
Execute the lsshe command to allow your system to work with older OpenSSH clients and servers. If you want to restore the default behavior (newer OpenSSH clients and servers block connecting with older OpenSSH clients and servers), then execute lsshe again.
If you don’t have OpenSSH server installed and setup when you run lsshe, but end up installing it later, no worries. The OpenSSH server will automatically pick up Legacy SSH Enabler’s custom configuration files.
If you have a RedHat Linux distribution (Fedora, CentOS, RHEL) you need to reboot your system after running lsshe for it to take effect.
Before Legacy SSH Enabler
After Legacy SSH Enabler
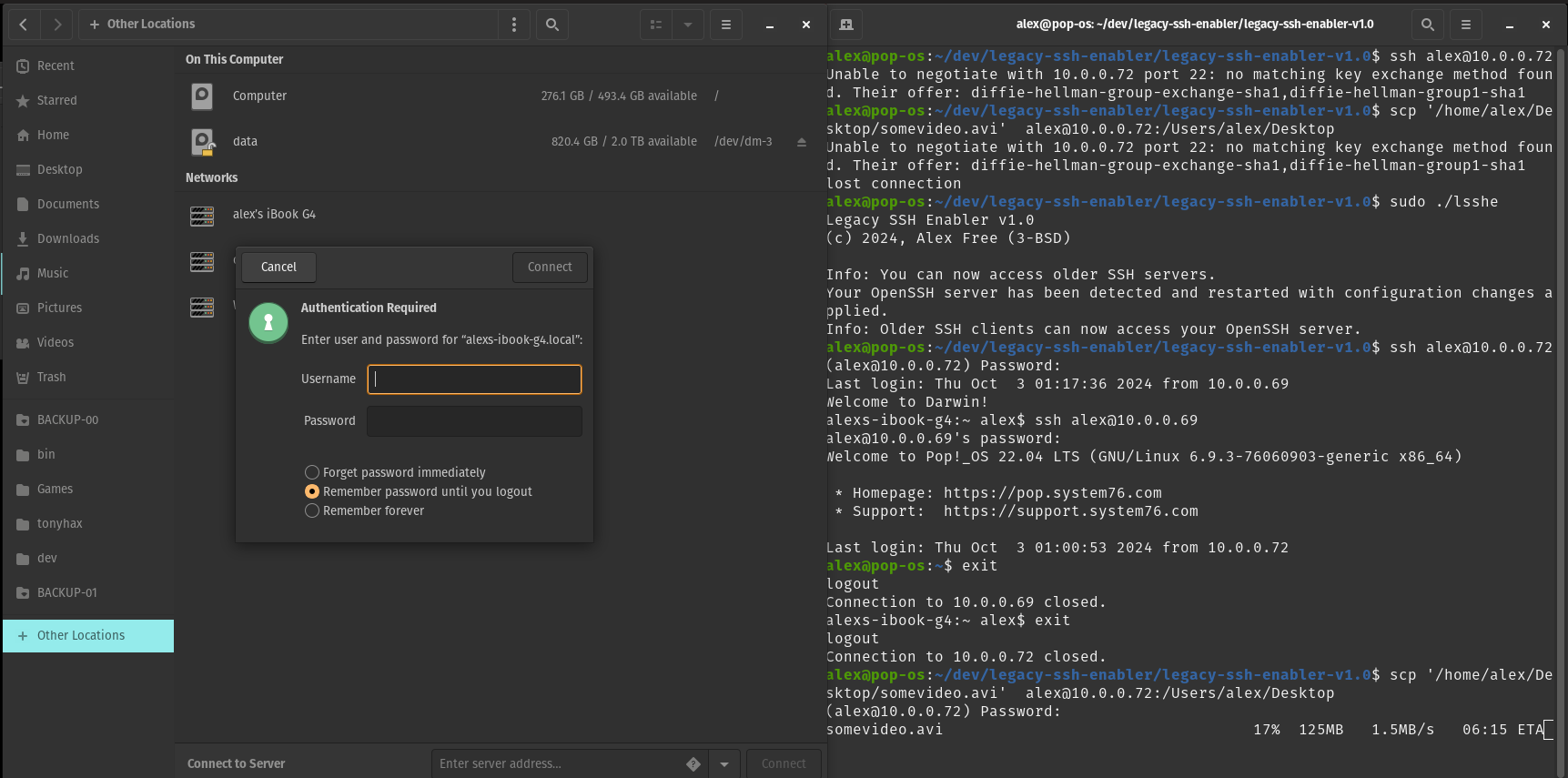
This is how much I like Visual Studio Code.
Why Is This Needed?
OpenSSH supports many different kex algorithms, ciphers, public key algorithms, and host key algorithms. Over the years better more secure and efficient ones have been implemented into new releases of OpenSSH. Eventually some of the oldest, weakest ones were disabled by default. That sounds like good thing, right? Just update all of your OpenSSH clients, and everything will work great again.
But what if you can’t (or don’t want to)? For example, I have Mac OS X 10.4 PowerPC computer. I just want to use the built in, ancient OpenSSH included in that OS over my local network. I don’t care how weak the encryption is when it’s all local network traffic.
How Does This Work?
There are other solutions that require you to add a bunch of arguments to your ssh command (i.e. ssh -o KexAlgorithms=+diffie-hellman-group-exchange-sha1 -o KexAlgorithms=+diffie-hellman-group1-sha1 -o HostKeyAlgorithms=+ssh-rsa alex@10.0.0.71 works to connect to Mac OS X 10.4’s default OpenSSH server). But this has some downsides (you have none of these after using Legacy SSH Enabler):
- You need to remember all of the arguments every single time you use
sshorscp. - You could create a wrapper script, but things on your system won’t use said wrapper (i.e.
Gnome Filescan’t open a SSH or SFTP connection to a legacy SSH server). - You still can’t connect to your main system’s modern SSH server from your older SSH client (i.e. I can’t SSH into my Linux laptop from Mac OS X 10.4’s default
sshcommand).
You can do so much better then wrapper scripts. What Legacy SSH Enabler does is adds 2 custom configuration files to your /etc/ssh/ssh_config.d and /etc/ssh/sshd_config.d directories. This doesn’t modify any existing OpenSSH configuration files directly, super cool. In addition, if the OpenSSH server is installed, it restarts the server with the new configuration files included automatically so that the changes take effect. The configuration files are not hardcoded, but rather generated dynamically based on of the capabilities of the currently installed OpenSSH client on your main machine. This is great future proofing design wise. Essentially, Legacy SSH Enabler asks for all of the KexAlgorithms, PubkeyAcceptedAlgorithms, HostKeyAlgorithms, and Ciphers supported by OpenSSH (irregardless of if they are not enabled by default). It then simply tells your OpenSSH to work with all of them!